Integrations with AWS Lambda then allow responding programmatically to monitoring signals by executing automation routines and notifications. CloudWatch Logs supplies a strong log aggregation pipeline throughout infrastructure and services. This centralized access delivers visibility for analytics that may otherwise require disparate querying throughout servers. The objective of steady monitoring is to get alerts when key efficiency indicators (KPIs) cross thresholds so you can continuous monitoring cloud examine and resolve issues proactively. These tools sift through the info, figuring out patterns, anomalies, and potential safety threats.

Cloud Monitoring: What It Is And Three Greatest Practices To Implement
Consider the prices of ISO certification relative to your organization’s dimension https://www.globalcloudteam.com/ and number of employees. Establish a system or protocol to regularly monitor your SOC 2 compliance and identify any breaches of your compliance, as this could occur with system updates and modifications. When you move your audit, the auditor will present you with your SOC 2 report to document and confirm your compliance. Complete a readiness evaluation with this auditor to determine when you have met the minimal standards to undergo a full audit. Using Vanta’s initial evaluation report, draft security insurance policies and protocols that adhere to the standards outlined in SOC 2.
Assumerolewithwebidentity What?! Solving The Github To Aws Oidc Invalididentitytoken Failure Loop
Monitoring tools provide perception into files, site visitors, availability, and so on., for cloud-hosted websites. Overall, website monitoring helps analyze person experiences to inform optimization efforts. The Threat Stack Security Operations Center enables end-to-end security oversight from a single platform. The tool uses machine studying and steady monitoring methods to surface anomalous habits in infrastructure and utility stacks. This makes it possible to watch every little thing from routers and switches to VPNs and firewalls. Here are some top network monitoring solutions for modern, multi-cloud networks.
What Is Continuous Monitoring In Devops?

Besides Cost Explorer, AWS presents several different cloud financial administration instruments. ProsperOps helps reduce commitment danger for short-term initiatives like testing and deployments. For instance, the platform may help you choose the right AWS occasion on your workload or project timeframe, permitting you to maximise savings while reaching optimum system efficiency. A current research reveals firms waste as a lot as 26 billion dollars or 33% of their cloud finances on everything from not rightsizing cloud assets to hourly charges on idle sources.
Paessler Prtg Network Monitoring – All-in-one Community Monitoring Device
Quzara offers predefined security controls which might be easily inherited into already present security infrastructure leading to simple implementation and immediate use. The cloud has reshaped digital infrastructure and operations for organizations, offering unmatched agility, scalability, and cost financial savings. As companies increasingly rely on the cloud for his or her IT infrastructure, ensuring seamless operations is important. Keep safety front and heart with a transparent dashboard across all your AWS and Azure environments, as nicely as automated, weekly assessments delivered instantly into your inbox. You’ll be succesful of quickly evaluate the latest at-risk resources so you presumably can take motion quickly.
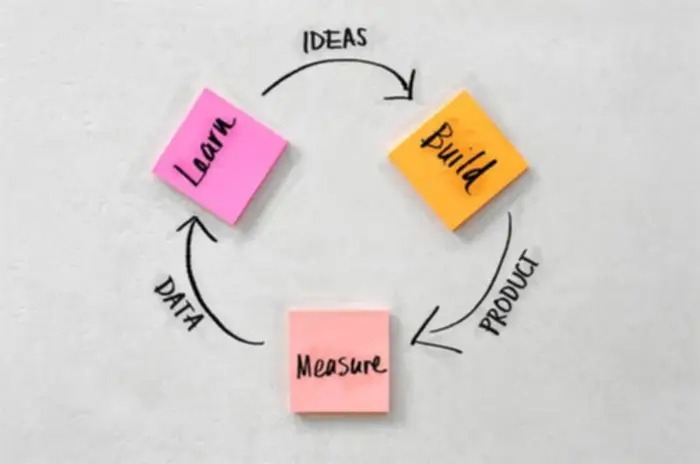
The Method To Implement Steady Monitoring
- Although it’s tempting to incorporate all techniques in your steady monitoring regimen, doing so can be unnecessarily cost-prohibitive and complicated.
- More techniques you have to use include HTTP requests, Ping, SQL, Rest APIs (returning JSON or XML), and so on.
- With Quzara, you can receive alerts and customized dashboards that provide steady visibility into your infrastructure, functions, and network.
- StackArmor’s ConMon team works as an built-in unit with the client’s cloud group and is based in Washington DC.
- This covers some important instructions for metrics, logs and alarms in CloudWatch for constructing a monitoring pipeline.
There are many alternative CSPs out there for the infinite cloud-based potentialities, and all CSPs have varied companies and instruments obtainable from them, and for them. What I even have reviewed are high-level concepts, but each buyer might need to dial in the specifics primarily based on their use cases and goals. IaC is used to deploy and configure cloud sources similar to compute, storage, and networking. It isn’t a new concept for the cloud, however the velocity at which environments change in the cloud is bringing IaC into the security spotlight.
Assets might simply come and go before they are often assessed by a conventional scan device. There are additionally quality third-party functions that can be utilized, a few of them even already FedRAMP licensed. Regardless of the service/tool used, the key right here is interfacing them with the combination layer of an current CDM or steady monitoring answer. This can occur via API calls to and from the solution, that are made attainable by the current CDM program requirements. Continuous controls monitoring (CCM) is a vital facet of making GRC processes extra automated, accurate, and actionable through expertise.

October Quarterly Launch: New-scale Exabeam Safety Operations Platform
Like different all-in-one cloud monitoring companies, SolarWinds screens database utilization, network performance, utility performance, and infrastructure health. Vanta goes past management monitoring and presents a dedicated Risk Management answer with options for automated risk scoring and reporting. The concept is to use a single solution to automate a bit of your GRC processes, making certain better productiveness. With Vanta, you presumably can seamlessly combine threat administration with CCM, making certain a constant view of the relationship between risks and controls. Thankfully, there is a resolution for each downside, and implementing applicable security tools will go a good distance in defending your techniques. This article will guide you thru the ten finest steady safety monitoring instruments for 2023.
Provides continuous awareness on how your organization is assembly international cyber requirements to simply comply with laws and requirements such as NIST, ISO 27001, PCI-DSS, GDPR, SWIFT, and extra. Building on its current capabilities, ChaosSearch plans to ship true multi-model knowledge entry by supporting full-text search, SQL, and machine studying queries against a single back-end knowledge store. Security and privateness require constant vigilance to sustain as your environment adjusts to changing enterprise circumstances and an evolving threat landscape. Here’s how Carbide Cloud Monitoring may help keep you on high of your safety recreation. It ingests information from multiple sources concurrently, transforms it, and eventually delivers it to a “stash” (such as Elasticsearch). With Kibana, you can visualize your monitoring data with graphs and charts in Elasticsearch.
A SIEM might help perceive this large quantity of information, arriving as many data streams in several formats, by normalizing and storing it in a central repository. A SIEM can correlate and aggregate knowledge to supply security insights and generate actionable alerts for security groups. Leveraging logs also permits you to correlate authentication and community events (and compare those to benchmarks) and spot suspicious activities like brute drive attacks, password spraying, SQL injection, or knowledge exfiltration. For example, the community logs might spotlight unusually large recordsdata moving out of your network, whereas authentication logs might match that activity to a specific consumer on a specific machine. Once the software program is released into production, Continuous Monitoring will notify dev and QA teams in the event of particular points arising within the prod surroundings.

For resources that are going to have some degree of persistence, agents are a great way to perform continuous monitoring. Agents can check in with a master to maintain up the inventory and in addition perform security checks as soon as the resource is spun up, instead of having to attend for a sweeping scan. Agents can be put in as a half of the build course of and even be made a half of a deployment picture.
Finally, we reveal how CloudWatch occasions can trigger automated actions and workflows via integration with AWS Lambda. A continuous monitoring system uses numerous units and agent plugins to gather data — corresponding to system logs, community traffic, and application activity — providing a gradual stream of data. The worth that continuous monitoring brings to your IT operations is greater visibility, which might result in accelerated and more focused incident responses. The sooner you notice errors, the sooner you presumably can begin the foundation cause analysis and the following remediation process. A centralized dashboard with Bitsight provides visibility throughout all of your attack floor to visualize areas of crucial or extreme risk and prioritize remediation. Bitsight additionally makes use of a cloud safety audit to find the hidden property and cloud situations common to shadow IT, serving to you to align with company security insurance policies.
